5G networks are the latest generation of cellular technology that promise faster speeds, lower latency, and improved connectivity.
One of the key differences between 5G and its predecessor, 4G, is the core network architecture.
The 4G core network, known as Evolved Packet Core (EPC), is based on a “flat architecture” where few network nodes are involved in handling traffic and protocol conversion is avoided.
However, 5G’s Enhanced Mobile Broadband (eMBB) service requires a more advanced, cloud-native core network to unlock its full potential.
How 5GC is Different than 4G EPC?
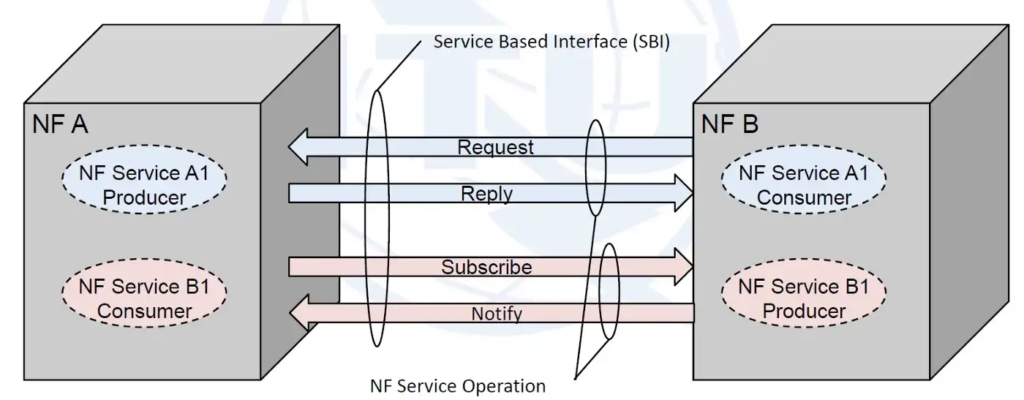
The major architectural difference between 5G Core (5GC) and Evolved Packet Core (EPC) is that 5GC utilizes the Service-Based Architecture (SBA) for control plane interactions.
One of the major differences between 5GC and EPC is the structure of their control plane (CP). 5GC has a different functional separation of Access and Mobility Functions (AMF) and Session Management Functions (SMF). This separation allows for more efficient scaling of resources and improved network performance.
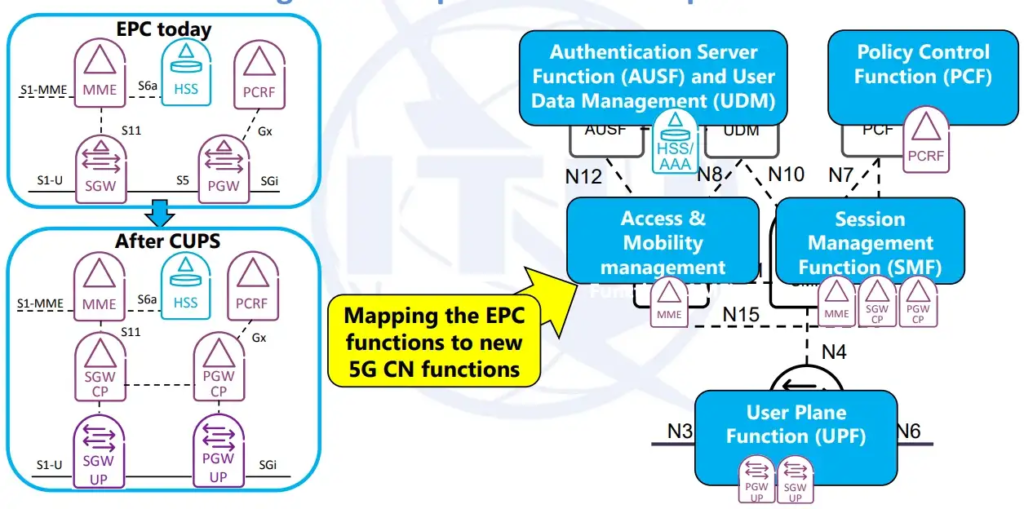
Additionally, 5GC includes the separation of User Plane (UP) and CP functions of the gateway. This feature, known as gateway CP/UP separation (CUPS), was introduced in EPC Release 14 and further enhanced in 5GC. This separation allows for more flexibility in deploying low-latency services in local data centers while maintaining centralized control plane functions.
SGW → SGW-C and SGW-U PGW → PGW-C and PGW-U
Another major difference in 5G’s control plane is the structure, which includes different functional separation of Access and Mobility Functions (AMF) and Session Management Functions (SMF). This allows for more granular control of network functions, and enables new services and use cases.
In addition to the functional separation of AMF and SMF, 5GC also introduces new functions such as the Network Slice Selection Function (NSSF) and the Network Exposure Function (NEF).
The NSSF enables the selection of the appropriate network slice for a specific service, while the NEF is responsible for exposing the capabilities of the network to the service layer.
Service-Based Architecture (SBA) principles are also applied to interfaces between CP functions within 5G, but not to interfaces toward Radio Access Network (RAN), user equipment or user plane (UP) functions (N1, N2, N3, N4, N6 and N9).
On another Side, The Evolved Packet Core (EPC) is a set of four core elements, introduced in 3GPP Release 8, that manage User Equipment (UE) connections and data flow.
The EPC elements are the Serving Gateway (SGW), the PDN Gateway (PGW), the Mobility Management Entities (MME), and the Home Subscriber Server (HSS).
The SGW manages User Plane (UP) data, the MME manages Control Plane (CP) functions, the HSS manages UE authentication, and the PGW connects the EPC to external IP networks. UE connects to the EPC through eNodeB base stations.
Comparison Table Between 4G EPC vs 5G Core Functionalities:
| Feature | 4G EPC | 5G Core |
|---|---|---|
| Components | Serving Gateway (SGW), PDN Gateway (PGW), Mobility Management Entity (MME), Home Subscriber Server (HSS) | AMF(Access and Mobility Functions), (Session Management Functions) SMF, (Authentication Server Function) AUSF, (Network Slice Selection Function) NSSF, (Network Exposure Function) NEF |
| Data Handling | SGW manages UP data, MME handles CP functions | Service-Based Architecture (SBA) for CP functions |
| Connectivity | Connects to external IP networks through PGW | Network slicing and granular distribution of NFs |
| Authentication | HSS manages UE authentication | Separate Authentication Server (AUSF) |
| Development | Traditional approach | Adoption of DevOps approach for cloud-native core network operation |
| Performance | Flat architecture for efficient data handling | Unlocking full potential of 5G for IoT and industrial automation use cases |
| Additional Functions | – | Network Slice Selection Function (NSSF), Network Exposure Function (NEF) |
| Functional Separation | – | Access and Mobility Functions (AMF) and Session Management Functions (SMF) separated |
5G Architecture Points
5G architecture is designed to support the diverse requirements of various services and use cases, including enhanced mobile broadband (eMBB), ultra-reliable low-latency communications (URLLC), and massive machine-type communications (mMTC).

Below are the 5G Architecture Key Functional Points:
Separation of User Plane and Control Plane
One of the main characteristics of 5G architecture is the separation of the user plane and the control plane. The user plane carries user traffic and the control plane carries signaling traffic in the 5GS.
The separation of the user and control planes enables each plane resource to be scaled independently. This means that the control plane can be scaled to handle signaling traffic, while the user plane can be scaled to handle user traffic.
Service-Based Architecture (SBA)
The SBA is the new architectural approach for 5G that separates the control plane and user plane functions.

The SBA allows for the development of new services and functions by creating a set of reusable and composable building blocks called “services.” The SBA also allows for the efficient management of resources and the ability to scale services as needed.
Parallel Access to Local and Centralized Services
5G architecture supports parallel access to local and centralized services. For example, the control plane can be centralized while the user plane with low-latency services can be deployed remotely in local data centers.
This allows for a more efficient use of resources and enables new business opportunities.
Radio Access Network (RAN)
The RAN is responsible for connecting the user equipment (UE) to the core network. The RAN includes the base stations (gNodeB) that handle the radio link with the UE and the base station controllers (AMF) that manage the connections between the base stations and the core network.
Additional Security Measures
5G System Security Architecture, which is designed to protect against new types of security threats such as Advanced Persistent Threats (APTs) and Distributed Denial of Service (DDoS) attacks.
5GC uses Network slicing which allows for the creation of multiple isolated and secure virtual networks within the same physical infrastructure, providing more flexibility and security for different types of services and use cases.
Furthermore, 5GC includes new security features such as identity-based access control and user plane integrity protection.
Efficiency and Flexibility
Finally, striving towards making operations as efficient as possible is key, while not forgetting the importance of flexibility to open up new business opportunities without bringing extensive or costly reconfigurations.
5G architecture is designed to be flexible and efficient, allowing for the deployment of new services and use cases without significant changes to the infrastructure.
Hope this article helped you out to know the all key differences between 4G EPC and 5G Core network architecture in details.
We have also published more such articles on 5G Core network and 5G Security for Core Security and 5G End-to-End Security in detail.