As 5G technology continues to roll out across the globe, the need for robust security measures to protect against threats and ensure the integrity of the network has become increasingly important.
One of the key security standards for 5G is 3GPP (3rd Generation Partnership Project), which is a collaboration between six telecommunications standards organizations that develop standards for mobile telecommunications.
Within 3GPP, the Security Group (SA3) is responsible for developing and maintaining security standards for 3GPP technologies, including 5G.
Another important security standard for 5G is ETSI (European Telecommunications Standards Institute), which is a European standardization organization that develops and maintains standards for information and communication technologies.
ETSI has developed a number of security standards for 5G, including the Network Functions Virtualization (NFV) Security Standard, which provides guidelines for securing virtualized network functions and services.
In addition to these standards, there are also a number of industry-specific security standards that apply to 5G, such as the GSMA (Global System for Mobile Communications Association) Security Standard, which is relevant for mobile network operators, and the 5G-ENS (5G Exchange Network Security) Standard, which is relevant for critical infrastructure providers.
5G Security Standards Includes:
- 3GPP (3rd Generation Partnership Project)
- Joint Technical Committee for IT
- NESAS (The Network Equipment Security Assurance Scheme)
- IETF
- ETSI
- NIST, GSMA, and Others
In this post, we would explore above mentioned and some other 5G security standards in more detail, exploring the specific measures they put in place to protect against threats and ensure the security of 5G networks.
5G 3GPP Security Standards
3GPP (3rd Generation Partnership Project) is a collaboration of telecommunications standards development organizations that is responsible for developing the technical standards for 5G and other mobile technologies.
3GPP has developed a number of security standards for 5G networks, including standards for encryption, authentication, and network security.
3GPP has also developed a number of security standards for 5G devices and user equipment, including standards for SIM cards, eSIMs, and Trusted Execution Environments (TEEs).
5G 3GPP Security Standards Points:
Below are the 5G 3GPP Security Standards Key Points:
1. AES (Advanced Encryption Standard)
AES (Advanced Encryption Standard) is a widely used encryption algorithm that is used to protect the confidentiality and integrity of data transmitted over 5G networks.
2. SSL/TLS
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are encryption protocols that are used to secure communications over 5G networks.
SSL and TLS use a combination of public key and symmetric key algorithms to provide strong encryption and authentication of data transmitted over the network.
3. EAP
EAP (Extensible Authentication Protocol) is a protocol that is used to authenticate devices and users accessing 5G networks.
EAP uses a variety of authentication methods, such as passwords, tokens, and certificates, to verify the identity of devices and users.
4. RADIUS
RADIUS (Remote Authentication Dial-In User Service) is a protocol that is used to authenticate and authorize devices and users accessing 5G networks.
RADIUS uses a central server to authenticate and authorize devices and users, and it can support a variety of authentication methods such as passwords, tokens, and certificates.
5G GSMA Security Standards
GSMA (GSM Association) is a trade organization that represents the interests of mobile operators worldwide.
GSMA has developed a number of security standards for 5G networks and devices, including standards for encryption, authentication, and network security.
Security Edge Protection Proxy (SEPP) is a key element of the 5G network architecture that is designed to protect the home network edge and act as a security gateway on interconnections between the home network and visited networks.
The SEPP is designed to provide application layer security, end-to-end authentication, integrity and confidentiality protection, key management mechanisms, and message filtering and policing.
In addition, the adoption of IP-based protocols such as HTTP/2, TLS, TCP, and the RESTful framework with OpenAPI 3.0.0 in 5G networks is expected to improve interoperability with a wider range of services and technologies, but may also increase the potential pool of attackers and the impact of vulnerabilities.
It is important for mobile operators and other stakeholders to be aware of these security risks and to adopt appropriate measures to mitigate them.
The GSMA is supporting the mobile security ecosystem through various programs and services such as:
- Fraud and Security Group (FASG), the Future Network Program
- The Coordinated Vulnerability Disclosure (CVD) Program
- IoT Security Project, and
- Networks Group (NG)
These programs and services can help to ensure the security of 5G networks, devices, and user equipment.
5G GSMA Security Standards Points
Below are the 5G GSMA Security Standards Points to consider:
For, Improved Confidentiality and Integrity of User and Device Data in 5G Networks:
1. Protects Confidentiality of Initial Non-Access Stratum (NAS) Messages
In 5G networks, the confidentiality of the initial non-access stratum (NAS) messages between the device and the network is protected, which makes it more difficult to trace user equipment (UE) using current attack methodologies over the radio interface. This helps to protect against man in the middle (MITM) and fake base station (Stingray/IMSI catcher) attacks.
2. Introduces Protection Mechanism Called Home Control
In 5G networks, a protection mechanism called home control is introduced, which means that the final device authentication to a visited network is completed after the home network has checked the authentication status of the device in the visited network.
This enhancement helps to prevent various types of roaming fraud that have been a problem for mobile operators in the past and supports the operator’s requirement to correctly authenticate devices to the services.
3. Supports Unified Authentication Across Different Access Network Types
In 5G networks, unified authentication is supported across different access network types, such as WLAN, allowing the 5G network to manage previously unmanaged and unsecured connections.
This includes the possibility of performing a re-authentication of the UE when it moves between different access or serving networks.
4. Supports User Plane Integrity Check
In 5G networks, user plane integrity checking is supported to ensure that the user traffic is not modified during transit. This helps to protect the integrity of the user data transmitted over the network.
5. Enhances Privacy Protection with use of Public/Private Key Pairs and Anchor Keys
In 5G networks, privacy protection is enhanced through the use of public/private key pairs and anchor keys to conceal the subscriber identity and derive keys used throughout the service architecture. This helps to protect the privacy of the user and device data transmitted over the network.
5G NIST Security Standards
NIST (National Institute of Standards and Technology) is a U.S. government agency that is responsible for developing technical standards and guidelines for a wide range of industries, including the telecommunications industry.
NIST has developed a number of security standards and guidelines for 5G networks, including standards for encryption, authentication, and network security.
5G NIST Security Standards Lists
1. Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) is a risk-based approach to managing cybersecurity that helps organizations to identify, protect, detect, respond, and recover from cyber threats. The CSF is designed to be flexible and adaptable, and it can be used by organizations of all sizes and in all sectors to manage cybersecurity risks.
2. Special Publication (SP) 800-53
NIST SP 800-53 is a set of security and privacy controls for federal information systems and organizations. SP 800-53 provides a comprehensive set of security controls that can be tailored to the specific needs of an organization, and it is designed to be used in conjunction with the NIST Cybersecurity Framework.
3. NIST SP 800-63
NIST SP 800-63 is a set of digital identity guidelines that provide recommendations for the secure issuance, management, and use of digital identities. SP 800-63 includes guidelines for the use of digital identities in 5G networks and devices, including guidelines for authentication, authorization, and identity proofing.
It is important for organizations to effectively manage 5G-related security risks as 5G becomes more widely available and to safeguard the technology from cyberattacks as it evolves.
To address these challenges, NIST is adopting an agile process to publish the 5G Cybersecurity project, which builds upon the work of the NCCoE’s Trusted Cloud project and focuses on a combination of 5G standards-based security features and a secure cloud-based hosting infrastructure.
The proposed solutions in the 5G Cybersecurity Practice Guide are intended to reduce risk and lower the likelihood of an incident occurring, strengthen the 5G network’s supporting infrastructure, safeguard the contents of 5G communications and the privacy of 5G users, and pave the way to zero trust by implementing demonstrated practices that mirror key zero trust principles.
By adopting these solutions, organizations can benefit from improved security and trust in their 5G networks and systems.
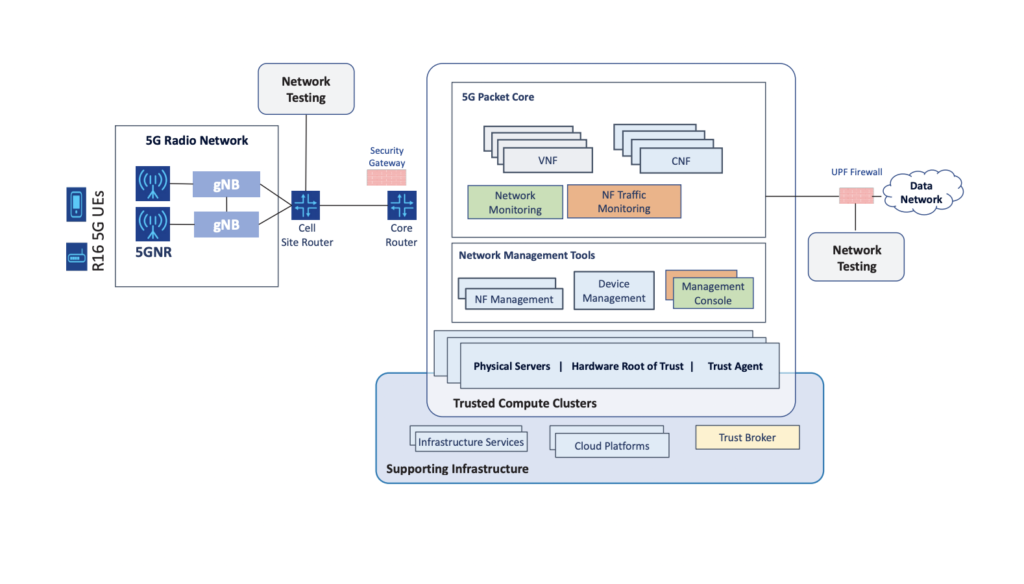
High-Level Architecture of the NCCoE 5G Implementation
The NIST Cybersecurity Center of Excellence (NCCoE) has developed a comprehensive guide called the NCCoE 5G Implementation that provides practical steps for organizations to implement these security standards in their 5G networks.
The NCCoE 5G Implementation guide covers various security areas such as identity and access management, network security, secure software development, and supply chain risk management.
It provides detailed guidance on how to implement security controls and technologies, including encryption, secure boot, secure communication protocols, and intrusion detection systems.
The goal of the NIST 5G security standards and the NCCoE 5G Implementation guide is to ensure that 5G networks are designed and implemented with robust security features that protect against potential cyber threats and attacks.
By following these guidelines, organizations can improve the security posture of their 5G networks and help ensure the confidentiality, integrity, and availability of their data and systems.
In below diagram, The architecture consists of the 5G radio access network (RAN) on the left side of the diagram, which includes 5G user equipment (UE), radios and antennas, and baseband units known as gNodeBs (gNBs).
The back haul network connects the RAN to the core network, which is located in a data center.
The data center is a key focus of the NCCoE’s example solution and includes supporting cloud infrastructure enabling trusted compute clusters, network management and security tools, and virtual and containerized 5G network functions.
This below mentioned NIST recommended architecture is designed to enable the implementation of a commercial-grade security reference architecture for 5G networks that bridges the gap between IT and telecommunications cybersecurity capabilities.
5G ETSI Security Standards
ETSI (European Telecommunications Standards Institute) is a standards organization that is responsible for developing technical standards for the telecommunications industry.
ETSI has developed a number of security standards for 5G networks and devices, including standards for encryption, authentication, and network security.
ETSI General Security Recommendations for 5G Systems
These requirements aim to mitigate bidding down attacks, ensure proper authentication and authorization, and provide confidentiality and integrity protection for user and signalling data.
To achieve these goals, the 5G system must support certain security features and algorithms, including encryption and integrity protection algorithms with keys of at least 128 bits, the use of ciphering for user data and signalling data, and support for various ciphering algorithms.
The 5G system must also support the secure storage of the Subscription Permanent Identifier (SUPI) in the user equipment (UE) and provide authorization based on the UE’s subscription profile obtained from the home network.
In addition, the system must support unauthenticated emergency services in certain regions, and must provide assurances to the UE that it is connected to authorized serving and access networks.
These security requirements are intended to ensure the confidentiality, integrity, and trustworthiness of 5G systems and networks.
ETSI General Security Recommendations for 5G Systems:
- Encryption and integrity protection algorithms with keys of at least 128 bits
- Use of ciphering for user data and signaling data
- Support for various ciphering algorithms
Additionally, The 5G system must also:
- Support secure storage of the Subscription Permanent Identifier (SUPI) in the user equipment (UE)
- Provide authorization based on the UE’s subscription profile obtained from the home network
- Support unauthenticated emergency services in certain regions
- Provide assurances to the UE that it is connected to authorized serving and access networks
Overall, these security requirements are described to ensure the confidentiality, integrity, and trustworthiness of 5G systems and networks.
Hope this article was able to help you out to understand the 5G Security measurements and standard recommendations provided by different organazation (3GPP, ETSI, NIST, GSMA) which are contributing to telecomm sector.
We have written some more articles surround 5G Security, you can read here: